Security at PSignite
Your security is our top priority.
Salesforce
Heroku
AWS
Secure solutions
Everything we do begins with security


Server security

Server security
Access to all machines is limited to the lowest number of people needed to keep them up and running. In addition, access via SSH has been disabled to prevent any unauthorized access to customer data.


Salesforce security review

Salesforce security review
Our products have successfully passed Salesforce Security Review. In the review, the Salesforce Security Team tests application defenses against the attacks described on the OWASP list. They replicate security threats by attempting to extract or modify data that they don’t have permission to access. Find more more information here.

Monitoring
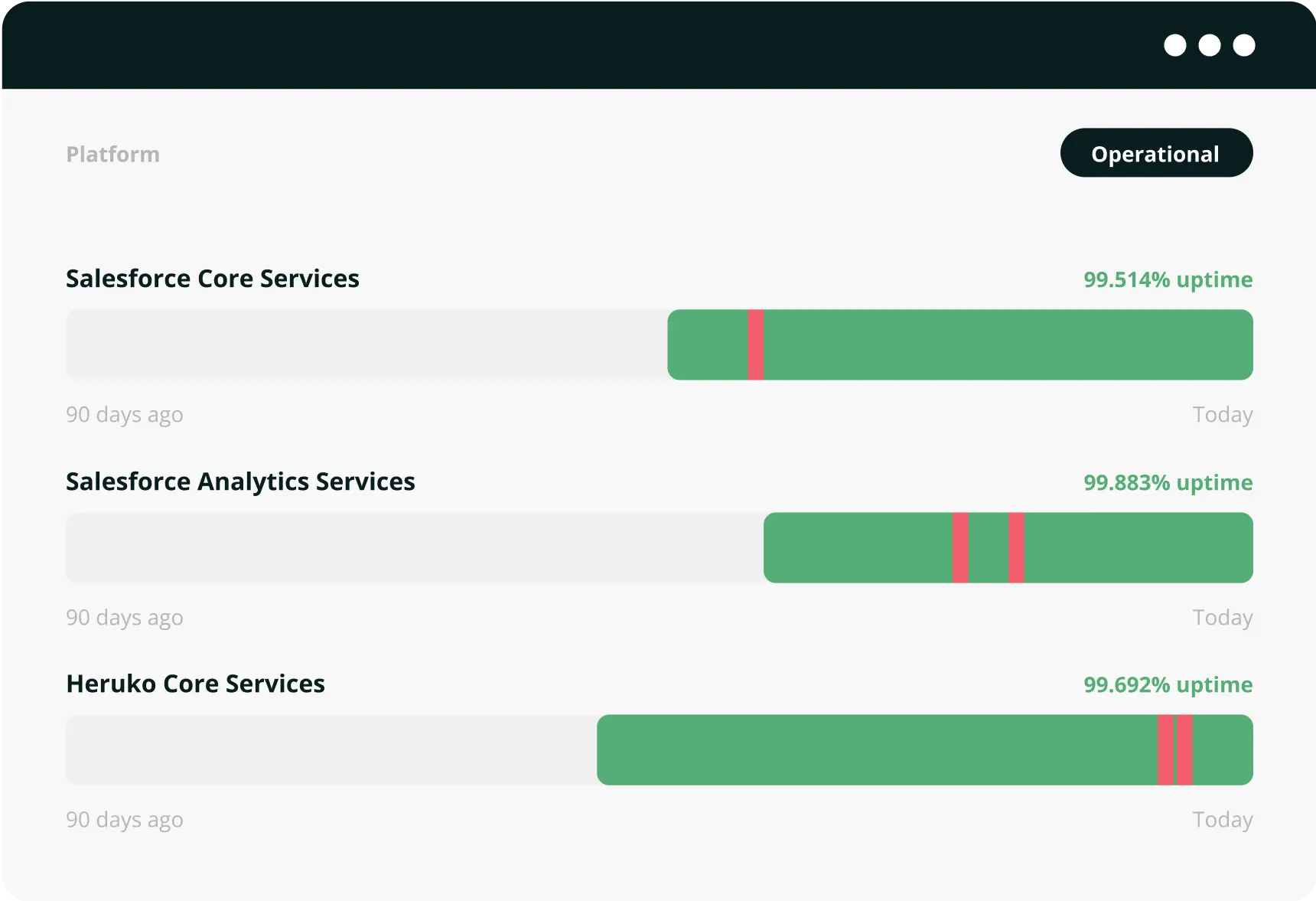
Monitoring
PSignite uses several third party services for monitoring the performance of the application. Find more in our Status Report.


Vulnerability management

Vulnerability management
In addition to internal security reviews, we use tools to scan our code for vulnerabilities including Snyk. Also, we use Vanta to continuously monitor our infrastructure, perform automated security tests, and verify compliance with security standards. Find more in our Trust Report.


Testing
Testing
We use several forms of testing to ensure changes are safe to be applied. Additionally, all application and infrastructure of code change requests require at least one peer review approval from another engineer before they enter the deployment pipeline.


CI / CD

CI / CD
We do not allow third party access to the codebase; all changes to the product are introduced by the PSignite Development Team. The CI/CD process in place guarantees smooth and automated deployments to all machines.

Server security
Access to all machines is limited to the lowest number of people needed to keep them up and running. In addition, access via SSH has been disabled to prevent any unauthorized access to customer data.

Salesforce security review
Our products have successfully passed Salesforce Security Review. In the review, the Salesforce Security Team tests application defenses against the attacks described on the OWASP list. They replicate security threats by attempting to extract or modify data that they don’t have permission to access. Find more more information here.

Monitoring
PSignite uses several third party services for monitoring the performance of the application. Find more in our Status Report.

Vulnerability management
In addition to internal security reviews, we use tools to scan our code for vulnerabilities including Snyk. Also, we use Vanta to continuously monitor our infrastructure, perform automated security tests, and verify compliance with security standards. Find more in our Trust Report.

Testing
We use several forms of testing to ensure changes are safe to be applied. Additionally, all application and infrastructure of code change requests require at least one peer review approval from another engineer before they enter the deployment pipeline.

CI / CD
We do not allow third party access to the codebase; all changes to the product are introduced by the PSignite Development Team. The CI/CD process in place guarantees smooth and automated deployments to all machines.
Data protection
We rigorously separate customer data, utilize certified data centers, and employ
secure technologies throughout our solution.
Data at rest
All data stores with customer data, in addition to S3 buckets (dedicated), are encrypted at rest. Sensitive collections and tables also use row-level encryption. This means the data is encrypted even before it hits the database so that neither physical access, nor logical access to the database, are able to read the most sensitive information.
Data in transit
Backups
All customer databases are backed up every day. Point-in-time-recovery allows the restoration of the database to any point in time within the previous seven days.
Data residency
Our servers are located in Salesforce, Heroku and AWS data centers, with options for data residency in the US or EU regions.
Data privacy
We only use customer data to offer our services. We do not share it with any third party nor use it for marketing purposes.
Secure your organization
At the organization level, you can create a complete list of approved users, set up the password approaches, and restrict logins to particular times/areas and IP addresses.

![]() Multi factor authentication
Multi factor authentication
![]() Single sign-on
Single sign-on
![]() Password policies
Password policies
![]() Login history
Login history
![]() Allowed login IP ranges
Allowed login IP ranges
![]() Allowed login hours
Allowed login hours
![]() Trusted IP ranges
Trusted IP ranges


-2.webp?width=314&height=160&name=Frame%2015708%20(1)-2.webp)
-2.webp?width=314&height=160&name=Frame%2015708%20(2)-2.webp)